Many times, during penetration tests, we have to monitor the data flowing inside the network. Achieving this on an Ethernet network is simple as we can just connect a network cable and be a part of the target network. But that makes us accountable and someone from the network can find out that someone is monitoring the traffic.
In wireless networks, we have an advantage of monitoring the network traffic passively. The packets are freely flowing over the air and we just need to be able to see them.
To be able to monitor network traffic, we must put our wireless adapter in Monitor mode.
airmon-ng start wlan0
This will start the monitor mode on a virtual interface such as “mon0”
To start dumping data from the target network, we need to know following things:
- BSSID – MAC address of the Access Point
- Channel on which the Access Point working
To find out these things, we can run airodump on all the channels. This will list all available wireless networks with various pieces of information for each network.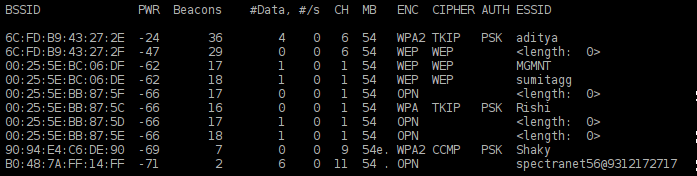
We can start dumping the data from target network using airodump-ng utility from aircrack-ng suite.
airodump-ng --bssid 90:F6:52:30:24:17 -w test_dump -c 1 mon0
This will start monitoring traffic on Access Point with BSSID = 90:F6:52:30:24:17 and channel =1 and the packets will be stored in a file named “test_dump”
After we have captured enough packets we can move on to extract data from the packets.
But this task is not as easy as it sounds.
The packets that are flowing through the air are encrypted and they must be decrypted for making them readable by other programs.
If we already know the passphrase for the network, we can decrypt the network traffic right away. In case we don’t know the password for the networks, we may have to take the following steps.
In case of WEP networks, the packets are simply encrypted using the passphrase as the key. We can easily find the key using aircrack-ng program if we have captured enough IVs and then move on to decrypt the packets.
There are many tutorials on how to crack WEP key, like this one
In case of WPA/WPA2 networks, the key is never transmitted over the air. This makes it a little difficult to attack. The key to finding the passphrase of WPA/WPA2 network is in the 4-way handshake which happens when a new client is connected to the network. If we have captured the 4-way handshake, we are good to go and crack the passphrase using aircrack-ng utility. If you haven’t captured a handshake, learn how to do that.
Assuming we have found the passphrase, we can decrypt the network traffic captured earlier using utility called airdecap-ng.
For WEP networks,
airdecap-ng -w <passphrase> test_dump-01.cap
For WPA/WPA2 networks,
airdecap-ng -p <passphrase> test_dump-01.cap
This will create a file with name test_dump-01-dec.cap which contains all the decrypted packets!
Now we can use this file and extract juicy data from it using tools like xplico, chaosreader, tcpxtract etc.
Thats all for passively capturing data over a wireless network. We can do much more when we have all the packets in our hands. More on that later.
This comment has been removed by the author.
ReplyDeleteNice share for me, maybe nice for all reader of your post.Patrick Henry Entropic
ReplyDeleteThanks for this post.I found so many details.I can fix my wireless doorbell now.
ReplyDeleteThanks for the valuable article. This is great! I’ll book mark this blog for future references. I’m glad I bump in to this blog. Wireless Network Solution Provider
ReplyDelete