Some time last year, I came across a Burp extension on Github that replicates the Invoke Applications functionality from OWASP ZAP in Burp. Since discovering this extension, it has become a very big part of my Burp workflow and probably one of the first extensions that I install on Burp. Surprisingly, I haven't seen anyone else using this extension and the Github project seems rather unknown to most people as well.
The extension I am talking about is "burp-send-to" by "bytebutcher".
PS: I couldn't find the original author of the extension on Twitter, if you know "bytebutcher", please reach out to me so that I can say thank you for their work on this and update their contact info. Bytebutcher contacted me via email :) Follow him on twitter and keep an eye for more awesome projects on his Github
Lets see what this extension is all about!
Core Idea
If you use BurpSuite regularly, you are probably familiar with sending requests from one tool to another tool within Burp. However, if you want to execute an external tool e.g. sqlmap or ffuf on an interesting endpoint, there is no native way of sending the request contents to these tools. In such cases, you have to either copy the URL or save the request as a file and then execute the desired tool yourself.
With "burp-send-to" (I will refer to the extension simply as "SendTo" from now on), you can invoke any external tool that you want with a predefined command. You can also pass any part of the request or response to the tool by using placeholders.
Installation
The SendTo extension can be downloaded from Github as a jar file and install by importing into Burp. The extension is also available in Burp's BApp Store but is an older version.
Usage
The extension creates a new tab "SendTo" which contains a few sample commands to showcase how to use the extension. On this tab, you can define and manage your own commands.
Following placeholders can be used within your commands:
- %H: will be replaced with the host
- %P: will be replaced with the port
- %T: will be replaced with the protocol
- %U: will be replaced with the url
- %A: will be replaced with the url path
- %Q: will be replaced with the url query
- %C: will be replaced with the cookies
- %M: will be replaced with the HTTP-method
- %S: will be replaced with the selected text
- %F: will be replaced with the path to a temporary file containing the selected text
- %R: will be replaced with the path to a temporary file containing the content of the focused request/response
- %E: will be replaced with the path to a temporary file containing the header of the focused request/response
- %B: will be replaced with the path to a temporary file containing the body of the focused request/response
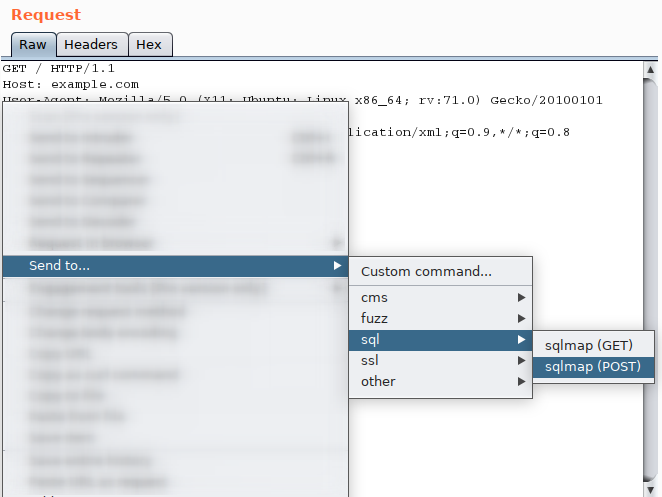
For example: if you normally execute sqlmap on any interesting URL, you can define the sqlmap command as:
sqlmap -u %U -f --dbs
The extension adds a right click context menu "Send to..." to allow sending the request/response to appropriate tool. So once you have identified an interesting request, simply right click on it and choose the command you wish to execute from the "SendTo" menu.
By default, the extension is configured to use xterm to run the commands. You can change it to anything you like. I use KDE so I have defined the terminal options as:
konsole --hold -e %C
Interesting use cases
- ffuf with custom wordlist:
I normally use FFUF with a wordlist using the following command:
ffuf -u <URL> -w wordlist -recursion -v -fs 0 -ac
I have defined this in SendTo as:
/path/to/ffuf -u %U -w /path/to/wordlist -recursion -v -fs 0 -ac
caveat: When you want to send a request to ffuf, first you need to send that request to Repeater, change the part which you want to fuzz with the FUZZ keyword and then use SendTo extension to invoke ffuf.
- gospider authenticated crawling
A very useful feature of gospider is the ability to use headers from a HTTP request with --burp flag. This allows gospider to crawl the authenticated parts of an application without providing credentials or doing weird auth recording routines that never work (looking at you Portswigger!)
I have defined this in SendTo as:
gospider --site %U --burp %R --concurrent 10 --depth 3 -o /tmp/ --proxy http://127.0.0.1:8080
This command invokes gospider on the selected URL and also passes the entire request body as a file so that gospider can extract headers and perform authenticated crawling.
- Hashcat to crack JWT
Want to send the JWT token to hashcat for cracking?
Just select the token and invoke SendTo with following command:
hashcat %F -m 16500 -a 3 -w 2 ?a?a?a?a?a
- smuggler
We all know the HTTP Request smuggler extension is great, but still want to execute the awesome smuggler.py script on a URL?
python /path/to/smuggler/smuggler.py -u %U
You can even select multiple URLs in Proxy history and send them all at once to any tool. You can also control whether the tool executes in parallel or in sequential fashion when multiple items are sent to a tool.
- Brute force numeric parameter with ffuf
A more advanced use requires some command-line fu but opens up a lot of possibilities when considering limitless potential of the command line. With the following command, you can bruteforce a numeric parameter using ffuf without ever going out of Burp:
bash -c "seq -w 0 5 | ffuf --request %R -w -:FUZZ"
In this command, we are generating the numbers from 0 to 5 (change this as per your requirements) and passing the generated numbers to ffuf as stdin.
In my experience, ffuf performs at least 10x faster than Burp Intruder.
We can probably completely replace Burp Intruder by replicating its functionality with ffuf by utilising tricks such as the above. Maybe a topic for another blog post ;)
As you can see, the extension adds powerful capabilities to Burp and has limitless possibilities to improve your workflow.
Wishlist
Despite all the wonderful features it already has, I wish the author adds a couple more features to make it even better
-
Automatic execution
Imagine you want to execute a particular tool on every request and response going through Burp while also passing relevant parts to the tool.
Piper can do this to some extent but I haven't figured out how to pass request contents to the tool.
-
Passing multiple inputs as single file
This seems pretty easy to implement. Something like selecting multiple URLs and passing all those URLs to a tool as file. Currently you can only pass the selected URLs directly on command line.
All in all, this is a wonderful little gem of an extension, kudos to bytebutcher for excellent work. Try it out and let me know how you are using it. Follow me on twitter for more such application security tidbits ;)
Comments
Post a Comment